Unified Threat Management Market Size and Forecast – 2025 – 2032
The Global Unified Threat Management Market size is estimated to be valued at USD 9.8 billion in 2025 and is expected to reach USD 19.4 billion by 2032, exhibiting a compound annual growth rate (CAGR) of 10.5% from 2025 to 2032.
Global Unified Threat Management Market Overview
Unified Threat Management products combine multiple network security functions into a single integrated platform. These typically include firewall protection, intrusion detection and prevention (IDS/IPS), VPN support, antivirus, antispam, web filtering, and application control. Designed to simplify security management, UTM appliances and software solutions provide centralized visibility and control over network traffic, ensuring comprehensive protection against evolving cyber threats in enterprise and SMB environments.
Key Takeaways
The Firewall solution type not only dominates the Unified Threat Management market but also continues to innovate with next-gen firewall features, driving substantial industry share growth.
In terms of deployment models, on-premises solutions remain prevalent; however, cloud-based and hybrid models exhibit faster growth due to enhanced flexibility.
Regionally, North America maintains the commanding market share given robust cybersecurity infrastructure and substantial IT spend, while Asia Pacific presents the fastest growth owing to digital transformation and rising cyber threats.
Furthermore, BFSI and government sectors consistently drive market demand, underpinned by stringent compliance norms and increasing security budgets.
Unified Threat Management Market Segmentation Analysis
To learn more about this report, Download Free Sample
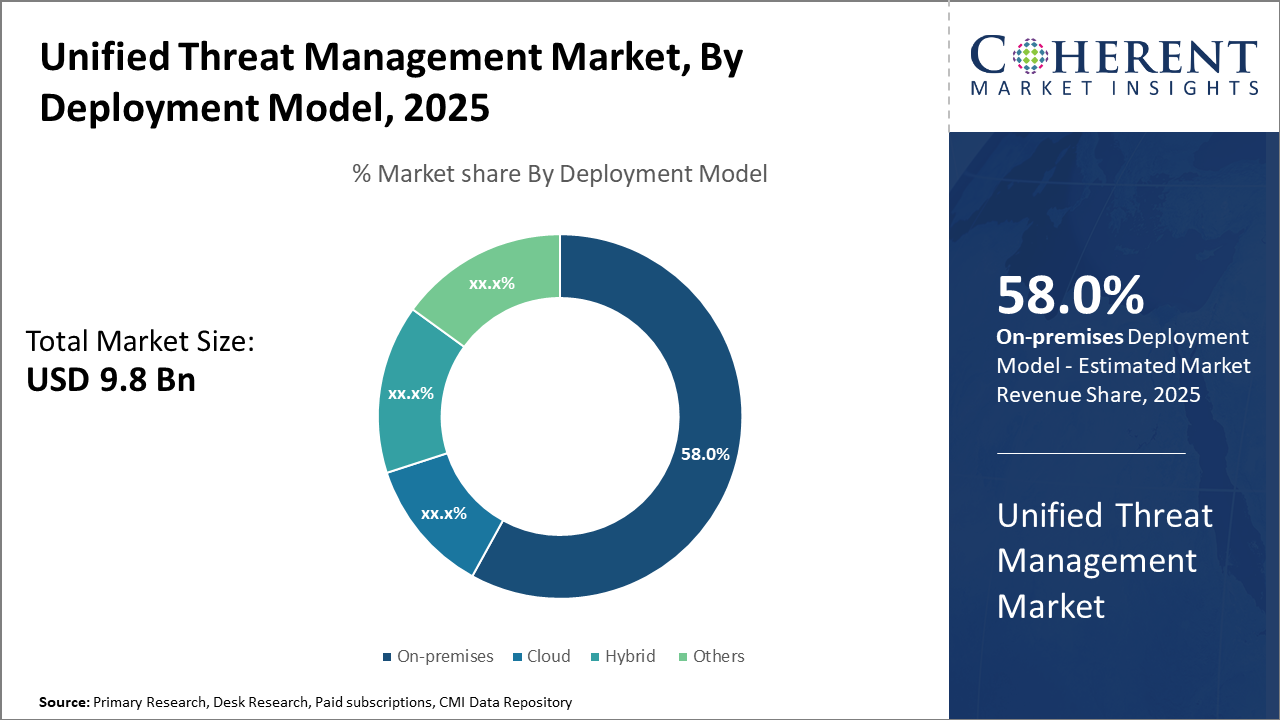
Unified Threat Management Market Insights, By Deployment Model
On-Premises segment is holding a dominant 58% market share, due to their enhanced control and data privacy, especially in regulated sectors such as government and financial services. However, the Cloud-Based deployment segment exhibits the fastest growth driven by enterprises embracing cloud infrastructures for agility and scalability, as cloud UTM deployments increased by 28% in 2024 globally. Hybrid models combining the benefits of both approaches are gaining traction, particularly in multinational organizations balancing data sovereignty with cloud adoption.
Unified Threat Management Market Insights, By Solution Type
Firewall dominates the market share with 32%, due to their foundational role in network security, integrating next-generation features such as application awareness and threat intelligence feeds. They effectively block inbound unauthorized access and mitigate advanced persistent threats. The fastest-growing subsegment is Email Security, reflecting a surge in phishing and business email compromise attacks, leading to increased investments in secure email gateways and filtering technologies.
Unified Threat Management Market Insights, By End-User
BFSI stands out as the dominating segment owing to its stringent regulatory frameworks and high exposure to cyber threats, driving substantial UTM adoption. The fastest-growing segment is Healthcare, where increasing digitization of medical records and IoT-enabled medical devices raise cybersecurity risks, compelling hospitals to invest heavily in unified security solutions. Government & Defense and IT & Telecom sectors also present robust demand, with government push for cybersecurity resilience and digital services expansion.
Unified Threat Management Market Trends
Recent market trends reveal that integrated cybersecurity approaches combining UTM with advanced threat intelligence platforms are redefining protective architectures.
The advent of cloud-native UTMs is transforming deployment models, with hybrid solutions enabling seamless security across multi-cloud environments.
Asia Pacific’s digital infrastructure enhancements, coupled with exploring AI functionalities in UTM, are major contributors to the market shift.
For example, in 2024, AI-enhanced UTMs achieved a 20% faster response time to zero-day vulnerabilities in pilot projects.
Another trend is the emergence of Zero Trust Network Access (ZTNA) frameworks interfacing with traditional UTM architectures to create multi-layered defense strategies.
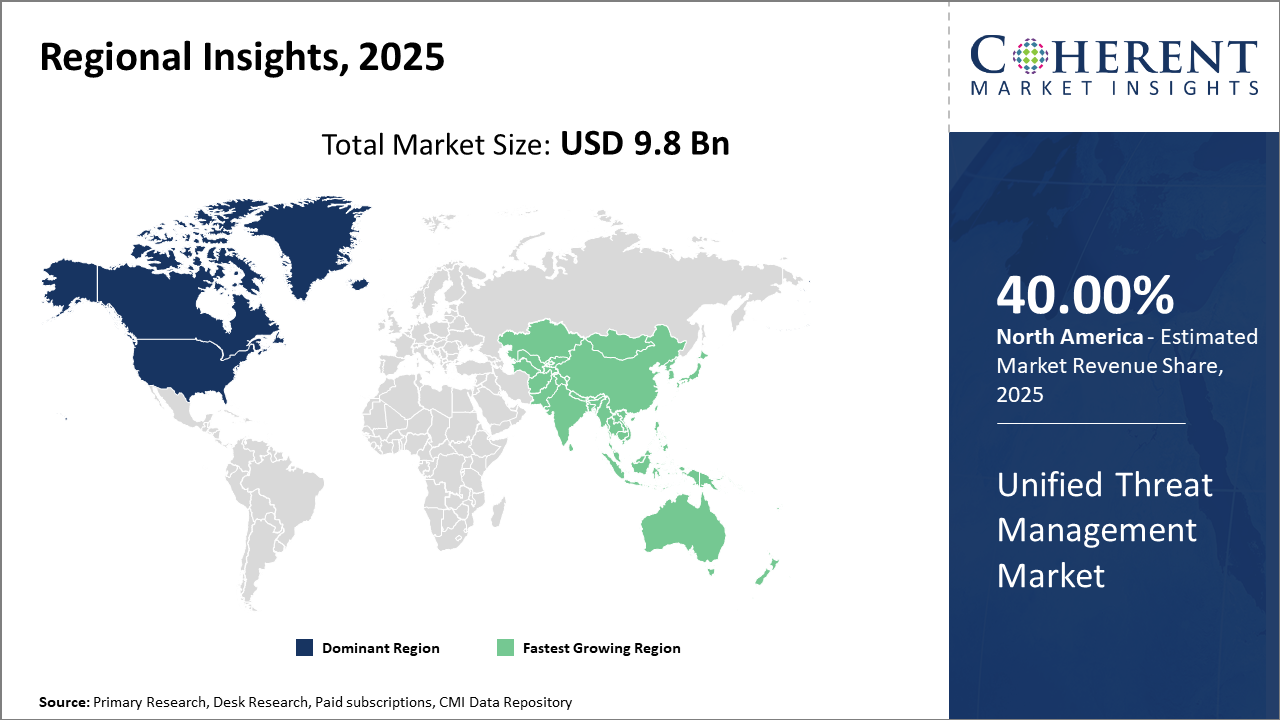
Unified Threat Management Market Insights, By Geography
To learn more about this report, Download Free Sample
North America Unified Threat Management Market Analysis and Trends
In North America, the dominance in the Unified Threat Management market stems from the presence of established industry players, coupled with significant IT and cybersecurity budgets. Stringent data protection laws and high awareness across industries contribute to a market share surpassing 40%. The U.S., accounting for the majority of this share, experienced a 15% increase in cybersecurity expenditure in 2024, supporting advanced UTM deployments at enterprise scale.
Asia Pacific Unified Threat Management Market Analysis and Trends
Meanwhile, Asia Pacific exhibits the fastest growth with a CAGR exceeding 13%, propelled by rapid digital transformation, government initiatives to fortify cybersecurity, and rising threats targeting connected infrastructure. Countries such as India and China are leading this expansion, driven by SMEs’ adoption of cost-effective and scalable UTM solutions.
Unified Threat Management Market Outlook for Key Countries
USA Unified Threat Management Market Analysis and Trends
The USA’s market is characterized by a mature cybersecurity ecosystem with dominant players like Cisco, Fortinet, and Palo Alto Networks spearheading innovation and market expansion. In 2024, U.S. corporate cybersecurity budgets rose by 18%, accelerating UTM refresh cycles and fostering integration with emerging technologies such as AI and cloud security. This ecosystem, supported by government mandates like the Cybersecurity Maturity Model Certification (CMMC), sustains the largest market share and sets benchmarks for global UTM adoption.
India Unified Threat Management Market Analysis and Trends
India’s UTM market is rapidly growing as enterprises increasingly invest in advanced security infrastructure to combat evolving cyber threats, aggravated by digital push initiatives like Digital India. Local companies alongside multinational vendors are driving penetration into SME and government sectors, with 2024 witnessing a 25% increase in UTM deployments. Favorable government regulations and growing cybersecurity awareness are key factors shaping India’s expanding market.
Analyst Opinion
Increasing adoption of integrated security solutions is propelling the Unified Threat Management market size as enterprises prioritize consolidated defenses. For instance, U.S.-based financial institutions reported a 22% rise in deployment of UTM appliances in 2024, a shift driven by regulatory compliance mandates and cost efficiency. This demand stems from the need to simplify cybersecurity layers without compromising effectiveness.
Pricing optimization and competitive bundling have enhanced the penetration of UTM solutions among SMEs globally. In 2025, nearly 45% of the new installations across Asia Pacific originated from SMEs adapting cost-effective UTM products that bundle firewall, intrusion detection, and VPN services, reflecting a significant demand-side market driver.
Export dynamics exhibit transformative growth for UTM vendors targeting emerging markets with evolving cybersecurity frameworks. Africa and Latin America have recorded a 30% increase in UTM imports in 2024, backed by government incentives targeting digital infrastructure security enhancement, further amplifying global market revenue streams.
Use case diversification, such as UTM deployment in cloud and IoT ecosystems, is expanding total addressable market scope. Enterprises in Europe exhibited an 18% increase in cloud-integrated UTM adoption in 2024, emphasizing the trend towards hybrid environment protection strategies that bolster business growth and threat resilience.
Market Scope
| Report Coverage | Details | ||
|---|---|---|---|
| Base Year: | 2025 | Market Size in 2025: | USD 9.8 billion |
| Historical Data for: | 2020 To 2024 | Forecast Period: | 2025 To 2032 |
| Forecast Period 2025 to 2032 CAGR: | 10.5% | 2032 Value Projection: | USD 19.4 billion |
| Geographies covered: |
|
||
| Segments covered: |
|
||
| Companies covered: | Cisco Systems, Fortinet, Check Point Software Technologies, Palo Alto Networks, Sophos, Juniper Networks, WatchGuard Technologies, Barracuda Networks, Trend Micro, SonicWall, Huawei Technologies, McAfee, Forcepoint. | ||
| Growth Drivers: |
|
||
Uncover macros and micros vetted on 75+ parameters: Get instant access to report
Unified Threat Management Market Growth Factors
The Unified Threat Management market growth is notably driven by increasing cybersecurity infrastructure investments amid soaring cybercrime rates highlighted by a 35% rise in global ransomware attacks in 2024. Hybrid work environments have pushed companies to adopt integrated UTM solutions, blending on-premises and cloud security for seamless protection. Regulatory compliance requirements such as GDPR and CCPA intensify demand for consolidated security tools, with 62% of European enterprises upgrading their UTM systems since 2023 to align with evolving standards. Additionally, the rapid proliferation of IoT devices has magnified network vulnerability, underpinning UTM market revenue expansion as enterprises seek scalable defense mechanisms.
Unified Threat Management Market Development
In August 2025, SonicWall launched nine new Generation 8 firewalls, featuring integrated Zero Trust Network Access (ZTNA), co-managed security services, and built-in cyber warranty. The launch strengthens MSPs’ and mid-sized enterprises’ cybersecurity capabilities by combining high-performance hardware with advanced threat protection in a single solution.
In October 2025, NETGEAR unveiled its Exium-powered Secure Access Service Edge (SASE) platform, integrating AI-powered zero-trust access, secure web gateway, SD-WAN, and firewall functions in a cloud-managed interface. The platform aims to provide SMEs with scalable, cost-effective network security and simplified management.
Key Players
Leading Companies of the Market
Cisco Systems
Fortinet
Check Point Software Technologies
Palo Alto Networks
Sophos
Juniper Networks
WatchGuard Technologies
Barracuda Networks
Trend Micro
SonicWall
Huawei Technologies
McAfee
Forcepoint.
Competitive strategies include Cisco’s portfolio expansion via acquisition of niche cybersecurity startups, enabling broader UTM solution suites that increased its market share by 4% in 2024. Fortinet emphasized channel partner engagement and innovation in AI-driven threat detection, leading to a 25% year-over-year revenue growth in North America. Sophos strengthened its cloud security capabilities through strategic alliances, facilitating accelerated penetration in Asia Pacific’s fast-growing SME segment.
Unified Threat Management Market Future Outlook
Future UTM products will evolve toward unified, cloud-native security platforms integrated into Secure Access Service Edge (SASE) frameworks. Artificial intelligence and machine learning will play major roles in automating threat identification and response, while support for edge computing and hybrid networks will become standard. As cybersecurity threats become more sophisticated, UTMs will incorporate behavioral analytics, zero-trust architecture, and API-based integration with external security tools. Moreover, vendors will emphasize modular product designs, subscription-based delivery, and centralized cloud management dashboards that deliver continuous updates without on-premise intervention. The long-term outlook points to UTMs functioning as a converged control hub for both on-premise and cloud security ecosystems.
Unified Threat Management Market Historical Analysis
Unified Threat Management systems first appeared in the early 2000s as a response to the complexity of deploying multiple standalone network security products. Initially, UTMs combined firewall, antivirus, and VPN capabilities into a single appliance designed primarily for small and medium enterprises. Over the years, UTM products expanded to include intrusion detection and prevention (IDS/IPS), web filtering, antispam, and application control. By the late 2010s, the emergence of virtualized networks and cloud infrastructure prompted vendors to transition from hardware-based boxes to software-defined and virtual appliances. Integration with central dashboards and real-time analytics improved visibility and simplified network administration, making UTMs an essential all-in-one defense layer.
Sources
Primary Research interviews:
Cybersecurity Analysts
Network Administrators
IT Security Managers
Cloud Security Experts
Databases:
Cybersecurity Ventures
Magazines:
SC Magazine
Cyber Defense Magazine
Infosecurity Magazine
CSO Online
Journals:
Computers & Security
Journal of Information Security
IEEE Security & Privacy
Network Security Journal
Newspapers:
The Economic Times (Tech)
The Washington Post (Cybersecurity)
The Guardian (Technology)
The Wall Street Journal (Tech Section)
Associations:
ISACA
(ISC)²
SANS Institute
Cybersecurity and Infrastructure Security Agency (CISA)
Share
Share
About Author
Suraj Bhanudas Jagtap is a seasoned Senior Management Consultant with over 7 years of experience. He has served Fortune 500 companies and startups, helping clients with cross broader expansion and market entry access strategies. He has played significant role in offering strategic viewpoints and actionable insights for various client’s projects including demand analysis, and competitive analysis, identifying right channel partner among others.
Missing comfort of reading report in your local language? Find your preferred language :
Transform your Strategy with Exclusive Trending Reports :
Frequently Asked Questions
Select a License Type
Joining thousands of companies around the world committed to making the Excellent Business Solutions.
View All Our Clients